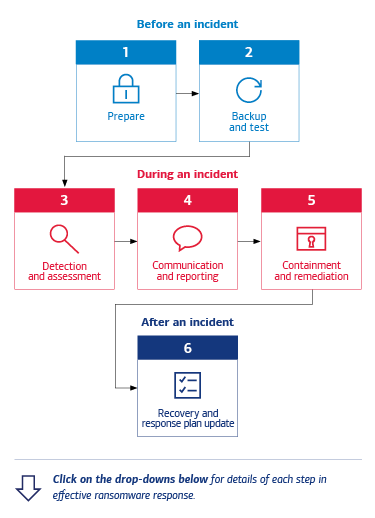
Ransomware represents a persistent threat for businesses in every industry. This type of cybercrime can have severe impacts on organizations in terms of financial and data loss, regulatory compliance issues and reputational damage.
Not all organizations that fall victim report these incidents to authorities, and scope and severity assessments may vary from one organization to another. This makes it difficult to capture the crime’s full impact. However, security experts and law enforcement agencies report more sophisticated ransomware actors1 using novel methods2 and inflicting more losses every year.3
Improved and better-integrated security controls can thwart many ransom attempts and sometimes expose bad actors’ movements before they accomplish their objectives. However, no security apparatus is perfect, and cybercriminals continue to devise new ways to cripple digital infrastructure and coerce targets into meeting their demands.