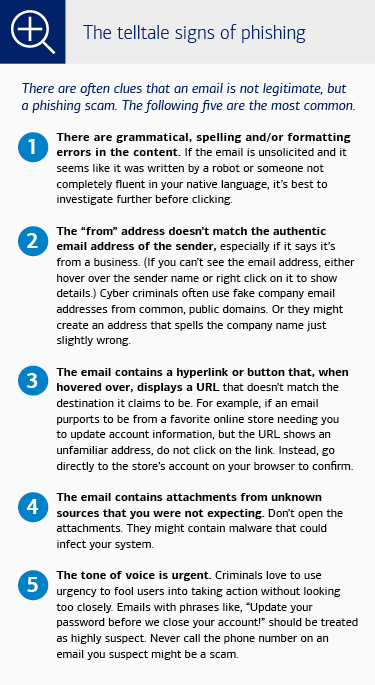
Some 30 years after the social engineering ploy known as phishing first emerged, the criminals behind it are as successful today as ever at tricking individuals into believing they are dealing with a legitimate party—costing people and organizations billions of dollars.
The international nonprofit Anti-Phishing Working Group reported almost five million phishing attacks in 2023 alone. And it can take less than a minute to fall victim to a phishing email according to the Verizon Data Breach Investigations Report. How has this scam been so successful for so long?
Cybercriminals rely on deception, urgency or too-good-to-be-true promises, and human tendencies like trust in authority, fear of missing out, greed or curiosity to get their targets to give up sensitive data such as login credentials and passwords, credit card numbers, account details, corporate contacts, vendor names or other proprietary information.
A phishing email may spoof a company, such as a bank or online shopping site, or look like it’s from an individual in authority or someone you know. It can include a link to a website that looks just like the real one, where cybercriminals collect usernames, passwords and other data they can sell on the black market, use to commit identity theft or drain bank accounts.
Criminals use information gathered from data leaks and social media accounts to deliver phishing scams that are more believable than ever—whether through text, voicemail or web search results. But you can outsmart the scammers by maintaining a healthy level of skepticism when receiving any kind of digital communication and shoring up your best defense: awareness.
Remember that Bank of America — and most other reputable companies — will never ask for account details unless you contact us first. If there’s any doubt, go directly to a trusted source, such as the company’s web site, or call to check using a phone number you can independently verify belongs to the company or individual who apparently sent the email.