- Card-not-present — This is where criminals are focusing most of their energy. Transactions occur via phone, mail, internet or other electronic means, and all that bad actors need is a card number, CVV, expiration date and address.
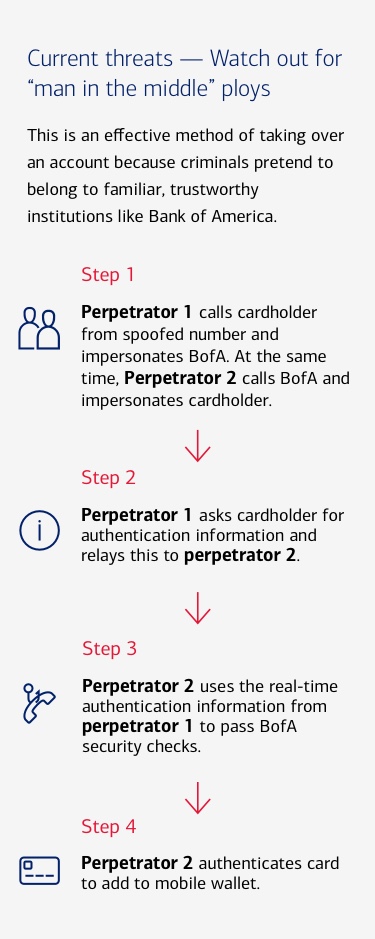
- Account takeover — Masquerading, phishing and smishing are used to get personal information and create new accounts. Criminals are increasingly targeting mobile wallets for in-person and card-not-present transactions.
- Card theft — With business travelers on the move again, the opportunity to physically steal cards has returned. Even though Chip and PIN adoption has taken off in the U.S., many terminals are set up to bypass PINs, meaning that fraudsters can often start to use a stolen card immediately.
How to protect your card program from fraud
Increased Chip and PIN adoption for corporate cards has made it harder for fraudsters to create and use counterfeits, leading them to embrace aggressive new tactics to compromise card programs.
7 minute read
Key takeaways
- The success of Chip and PIN has made counterfeit cards harder to create.
- Card-not-present is now the fastest-growing type of card fraud.
- There are actions that businesses and cardholders can take to prevent and detect fraud attempts.
Here are three leading fraud trends to be aware of:
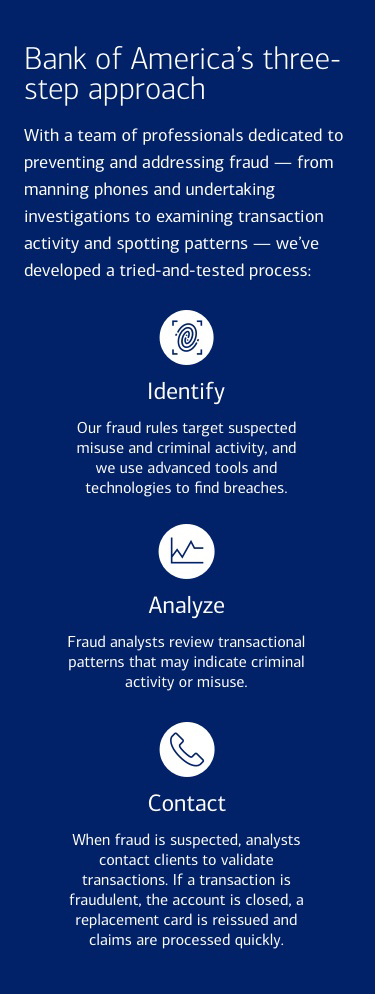
Fraud prevention is a team effort
What can businesses do?
Review transactions and report suspicious activity
- Gain full visibility into transactions by using all the applications and alerts at your disposal, and report anything suspicious immediately.
- Make sure you’ve reconciled all transactions before you pay, requesting receipts for payments made via peer-to-peer money transfer apps.
- Build an audit program where you review either a sample set or specific types of transactions to help spot misuse at an early stage.
Set up appropriate controls
- Establish merchant category codes and define who gets a card in your organization, as well as what they can do with it.
- Build in checks and balances by segregating card request and approval duties, with a minimum of two program administrators.
- Cancel department cards every time a cardholder leaves the company.
- Ensure credit limits are appropriate to each role.
Pay attention to prevention
- Don’t give power to fraudsters by using the same passwords across everything. Criminals can take advantage by using automation to match compromised data with commonly used passwords.
- ·Consider expanding your use of tools like mobile wallet — virtual payments are safer because they generate a one-use number for each transaction.
What can cardholders do?
Be vigilant and proactive
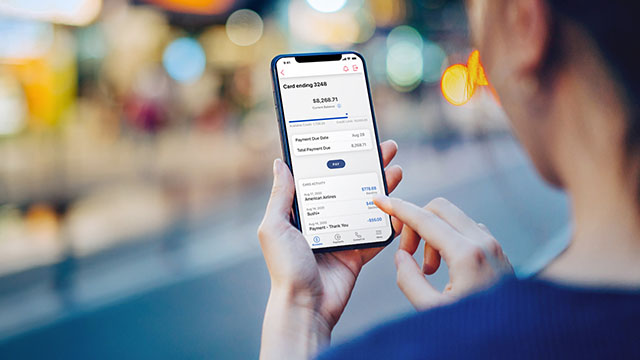
- Set up mobile alerts — what makes a business card different from a personal one is that you may only use it several times a year, so real-time visibility is key.
- Look at statements and report any suspicious activity as soon as you spot it.
Make the most of Chip and PIN protections
- Use Chip and PIN wherever you can — most merchants now have terminals with chip technology.
- Know your PIN and minimize declined transactions by recovering forgotten PINs with tools available on our mobile application.
Aim for accuracy
- Don’t let transactions get declined due to incorrect data.
- Verify name, address and CVV (3-digit code) for online transactions to ensure that a purchase goes through.
Global Card Access
Transform your business with an all-in-one commercial card management tool that delivers superior usability and security for cardholders and program administrators.